ReLiSys
- Contact:
- Project group:
Prof. Becker
- Funding:
ZIM of the German Federal Ministry for Economic Affairs and Climate Action (MBWK)
FKZ: ZF4011810DH9 (KIT)
- Partner:
Wibu-Systems AG, emmtrix Technologies GmbH, Forschungszentrum Informatik (FZI), KIT (ITIV & CES)
- Startdate:
01.01.2020
- Enddate:
30.06.2022
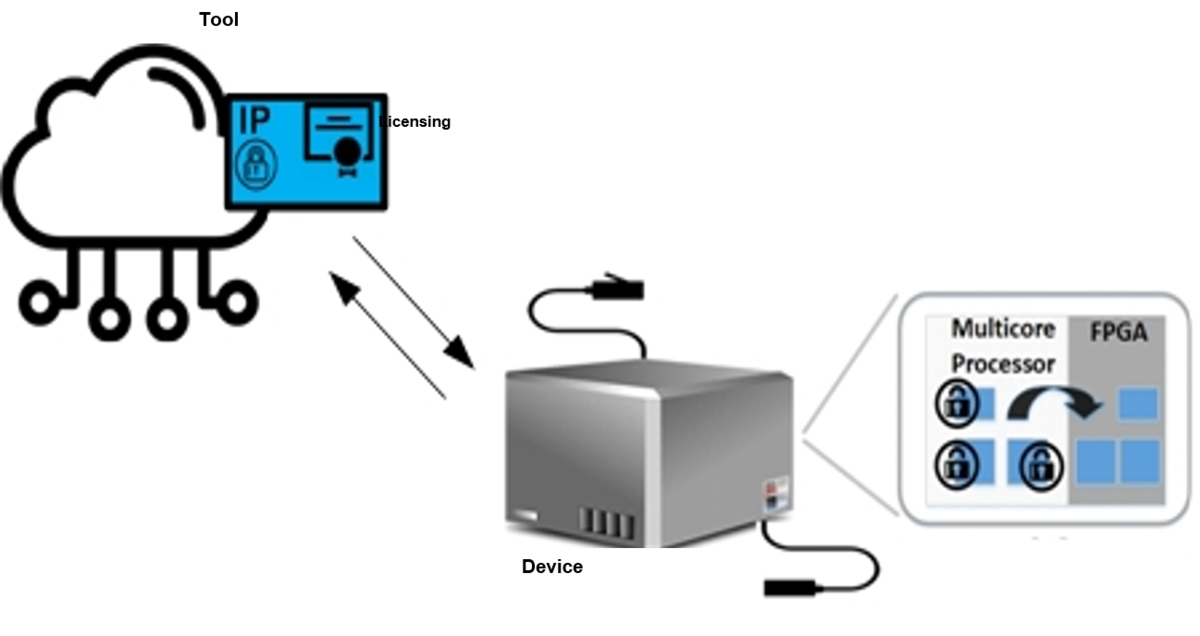
ReLiSys – Remote Configuration of Licensable-IP in FPGA Systems
![]()
Project goals
The project goals range from developing an “Independent IP Generation Framework,” developing a “Flow for Establishing Trust on a Device,” to analyzing attacks such as side-channel attacks and trojan infection in IP cores, including developing countermeasures to the attacks. A tool is being developed that leverages FPGA vendors’ EDA tools to create a standard base design that can be used by multiple parties involved in IP core licensing. Multiple Core Vendors (CVs) of IP cores and the System Developer (SD) of a device can share the tool to create IP cores that can interoperate on the device without exposing them to each other. The target device, the FPGA, can be vulnerable to IP theft through various attacks. The attacks of a device will be analyzed, and corresponding countermeasures will be developed to create flow for establishing trust on a device. Furthermore, the framework ensures that IPs can only be configured on the devices at the tool-level for which they have been licensed by the CV implementing a pay-per-device licensing scheme. In addition, other features are implemented, such as countermeasures for side-channel attacks (SCAs) and Trojan detection at the device.
ITIV participation
ITIV mainly participates in defining security requirements of the flow for establishing trust on a device, implementing trojan detection, and integrating the detection in the device. The trojan detection module can be added to the CV tool or the secure operating system of the target device's multicore processor (CPU). A partially reconfigurable IP core with or without trojan insertion at the tool level will be the primary source for trojan detection in the tool or the device.